OPENING POST
Description
Source packages should be able to access custom headers that they must send when requesting data from the APIs.
Examples
The most obvious example is the Authorization header:
- Basic Auth:
Authorization: Basic YWFhOmJiYg - JWT Auth:
Authorization: Bearer XXXXX.YYYYY.ZZZZZ
Possible solution (not finally used)
We could use state.source.headers for this.
- If a user needs to add headers for a specific site, they can do so in their
frontity.settings.jsfile. - If a package needs to set a header, they can do so by modifying the
state.
const state = {
source: {
headers: {
Authorization: "Basic YWFhOmJiYg",
},
},
};
Sometimes packages may want to authenticate only in the server but don’t expose the header in the client. For that reason, we can run the afterSSR action (which is pretty useless right now) before getting the state snapshot, like this:
- Run
init. - Run
beforeSSR. - Render HTML with React.
- Run
afterSSR. - Get
statesnapshot. - Send HTML +
stateto the client.
If a package doesn’t want a header to be exposed to the client, they will be able to delete it using the afterSSR action.
Related Feature Discussions
SUMMARY
Please, bear in mind that this section wasn’t part of the opening post. It has been added afterwards and its purpose is to keep a quick summary with the most relevant information about this FD at the top of the thread.

 . I guess this would be a horrible API but I’m mentioning it anyway.
. I guess this would be a horrible API but I’m mentioning it anyway.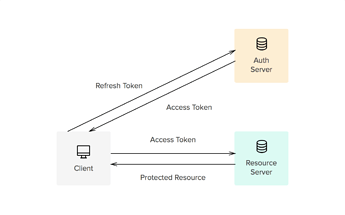




 :
: